In December 2018, KrebsOnSecurity looked at how dozens of U.S. political campaigns, cities and towns had paid a shady company called Web Listings Inc. after receiving what looked like a bill for search engine optimization (SEO) services rendered on behalf of their domain names. The story concluded that this dubious service had been scamming people and companies for more than a decade, and promised a Part II to explore who was behind Web Listings. What follows are some clues that point to a very convincing answer to that question.
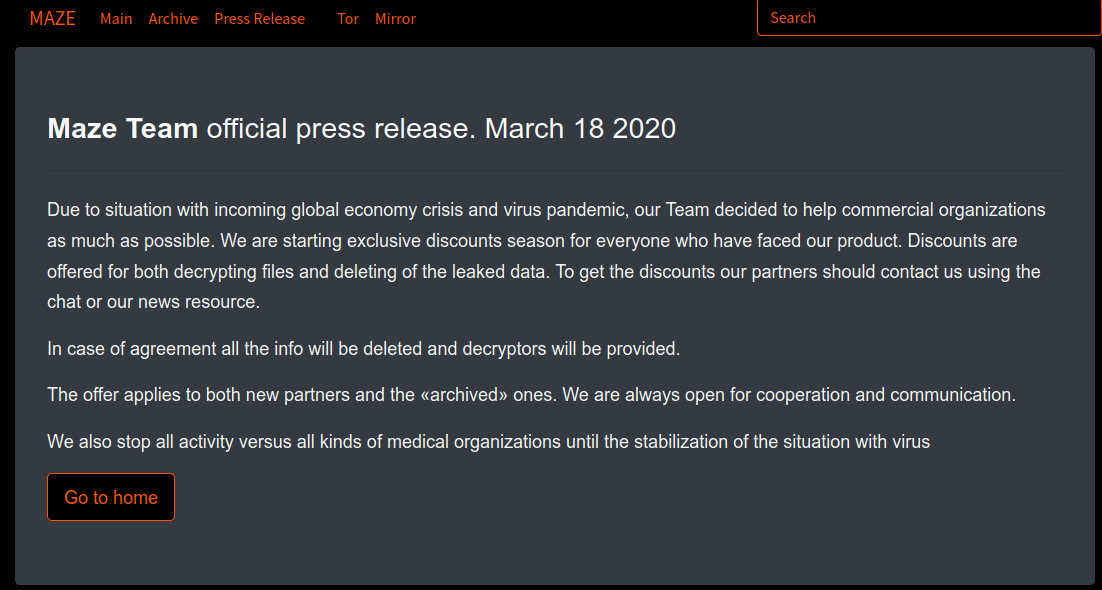
Since at least 2007, Web Listings Inc. has been sending snail mail letters to domain registrants around the world. The missives appear to be an $85 bill for an “annual search engine listing” service. The notice does disclose that it is in fact a solicitation and not a bill, but wording of the notice asserts the recipient has already received the services in question.

Image: Better Business Bureau.
The mailer references the domain name web-listings.net, one of several similarly-named domains registered sometime in 2007 or later to a “James Madison,” who lists his address variously as a university in New Britain, Connecticut or a UPS Store mailbox in Niagara Falls, New York.
Some others include: weblistingservices.com, webservicescorp.net, websiteservicescorp.com, web-listingsinc.com, weblistingsinc.net, and weblistingsreports.net. At some point, each of these domains changes the owner’s name from James Madison to “Mark Carter.” As we’ll see, Mark is a name that comes up quite a bit in this investigation.
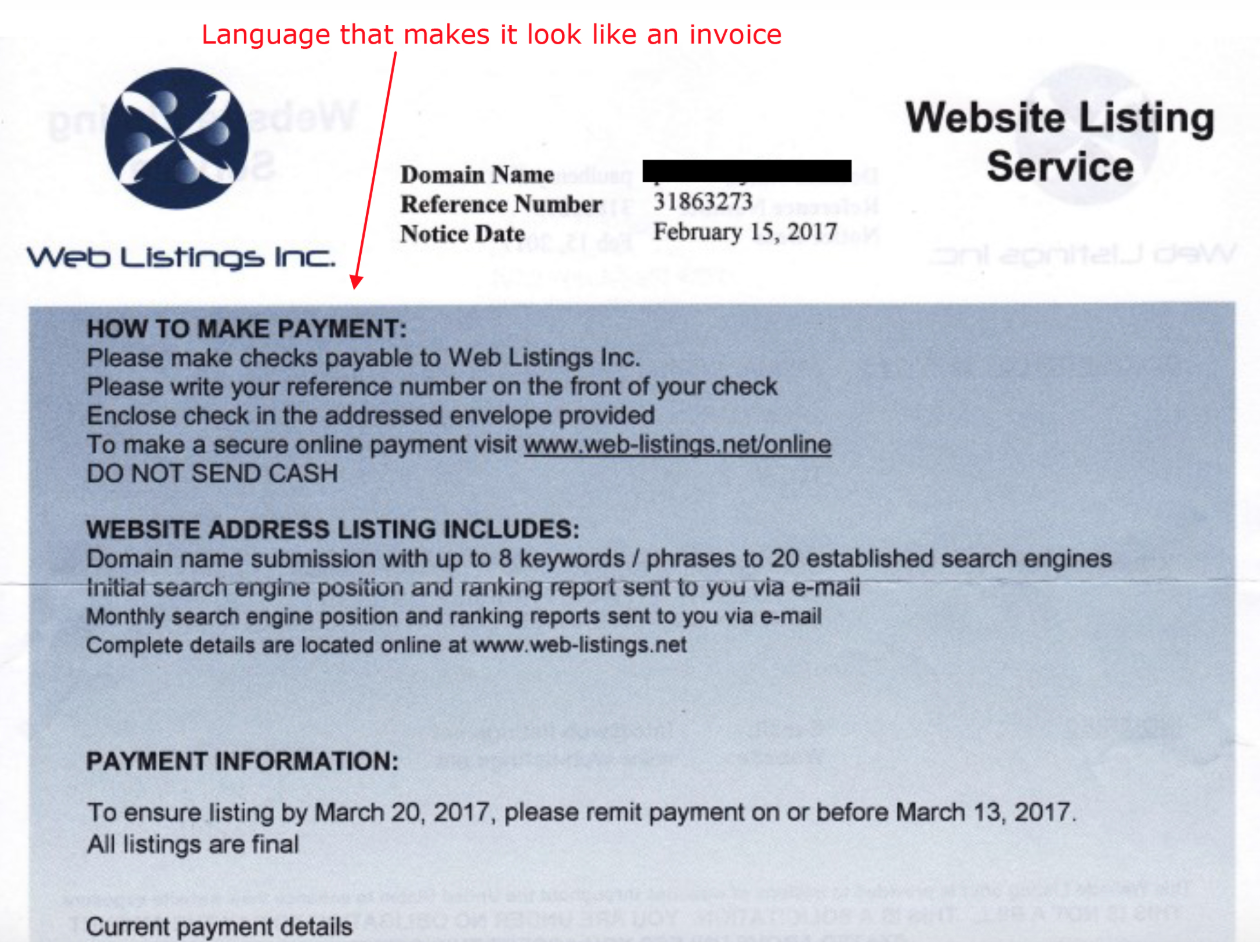
Image: Better Business Bureau.
A Twitter account for Web Listings Inc. has posts dating back to 2010, and points to even more Web Listings domains, including weblistingsinc.org. Cached versions of weblistingsinc.org at archive.org show logos similar to the one featured on the Web Listings mailer, and early versions of the site reference a number of “business partners” in India that also perform SEO services.
Searching the Internet for some of these Web listing domains mentioned in the company’s Twitter account brings up a series of press releases once issued on behalf of the company. One from May 2011 at onlineprnews.com sings the praises of Weblistingsinc.info, weblistingsinc.org and web-listings.net in the same release, and lists the point of contact simply as “Mark.”
Historic WHOIS registration records from Domaintools [an advertiser on this blog] say Weblistingsinc.org was registered in Nov. 2010 to a Mark Scott in Blairgowrie, Scotland, using the email address clientnews@reputationmanagementfor.com.
Reputationmanagementfor.com bills itself as an online service for “fighting negative and incorrect content on the internet,” which is especially interesting for reasons that should become clearer in a few paragraphs. The site says Mark Scott, 46, is an employee of Reputationmanagementfor.com, and that he is also involved with two other companies:
-GoBananas, a business that sets up group outings, with a focus on bachelor and bachelorette parties;
-HelpMeGo.to, a entity in Scotland that did online marketing and travel tourism both in Scotland (via sites like Scotland.org.uk and marketinghotelsonline.co.uk) and on India’s coastal Kerala state where HelpMeGo.to employed a number of people involved in the SEO business. Helpmego.to now simply redirects to GoBananas.
According to Farsight Security, a company that keeps historic records of which Web sites were hosted at which Internet addresses, Weblistingsinc.org was for a while hosted at the IP address 68.169.45.65 with just six other domains, including travelingalberta.com, which was a blog about traveling and living in Alberta, Canada registered to Mark Scott and the email address management@helpmego.to. Cached versions of this site from 2011 show it naming Web Listings Inc. as a business partner.
That same management@helpmego.to email address is tied to the WHOIS records for markscottblog.com, gobananas.co.uk, gobananas.com. Cached copies of markscottblog.com from 2010 at Archive.org show his profile page on blogger.com links to another blog with much the same content, images and links called internetmadness.blogspot.com.
Among the 2011 entries from the Internetmadness blog is a post promoting the wonders of benefits of Web Listings Inc.
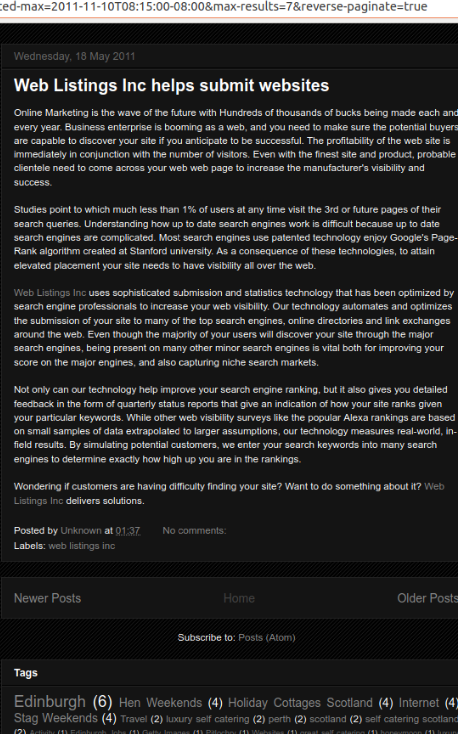
A cached copy of Mark Scott’s blog Internet Madness from 2011 promotes Web Listings Inc.
THE COBRA/APPCO GROUP
Aha! But wait, there’s more. You see, for years Weblistingsinc.org was hosted on the same servers along with a handful of other domains that all switched Internet addresses at the same times, including gobananas.com, gobananasworld.com and the IP addresses 107.20.142.166 (17 hosts), 54.85.65.241 (6 hosts).
Most of the other domains at these IPs historically have been tied to other domains connected to Mark Scott and his various companies and business partners, including chrisniarchos.net, redwoodsadvance.net, gdsinternationalus.com, staghensscotlands.com, cobra-group.blogspot.com, the-cobra-group.com, appcogroup.co.uk, and reputationmanagementfor.com.
I found a similar pattern with domains stemming from a Crunchbase company profile on Web Listings Inc., which says the firm is based in Toronto, Canada, with the Web site webtechnologiesinc.net, and email address webtechnologiesletter@gmail.com. Historic WHOIS data from Domaintools.com says Webtechnologiesinc.net was registered in 2013 to a Marcus Ruskov in Toronto.
Information about who registered Webtechnologiesletter.com is completely hidden behind privacy protection services. But Farsight says the domain was in 2015 hosted at the Internet address 54.77.128.87, along with just 70 other domains, including the same list of domains mentioned above, chrisniarchos.net, redwoodsadvance.net, gdsinternationalus.com, et cetera.
What do all of these domains have in common? They are tied to companies for which Mark Scott was listed as a key contact. For example, this press release from 2o11 says Mark Scott is the contact person for a company called Appco Group UK which bills itself as a market leader in face-to-face marketing and sales.
“Worldwide, Appco Group has raised hundreds of millions of pounds for some of the world’s biggest charities, delivered pay-TV and broadband services, financial services, security and many other successful marketing solutions on a diverse range of products,” the press release enthuses.
The Appco Group is the re-branded name of a family of marketing and sales companies originally created under the name The Cobra Group, whose Wikipedia page states that it is a door-to-door selling and marketing company headquartered in Hong Kong. It says investigations by the media have found the company promises much larger compensation rates that employees actually receive.
“It is also criticized for being a cult, a scam and a pyramid scheme,” the entry reads.
The Cobra Group and its multifariously named direct sales and marketing companies are probably best described as “multi-level marketing” schemes; that is, entities which often sell products and/or services of dubious quality, use high-pressure sales tactics and misleading if not deceptive advertising practices, and offer little to no employee payment for anything other than direct sales.
Even the most cursory amount of time spent searching the Internet for information on some of the companies named above (Appco Group, Cobra Group, Redwoods Advance, GDS International) reveals a mountain of bad press and horrible stories from former employees.
For example, Appco salespeople became known as “charity muggers” because they were trained to solicit donations on behalf of charities from random people on the street, and because media outlets later discovered that the people running Appco kept the majority of the millions of dollars they raised for the charities.
This exhaustive breakdown on the door-to-door sales industry traces Cobra and Appco Group back to a long line of companies that simply renamed and rebranded each time a scandal inevitably befell them.
Now it makes sense why Web Listings Inc. had so many confusingly-named domain names. And this might also explain the primary role of Mr. Scott’s business — the online reputation management company reputationmanagementfor.com — in relation to the Cobra Group/Appco’s efforts to burnish its reputation online.
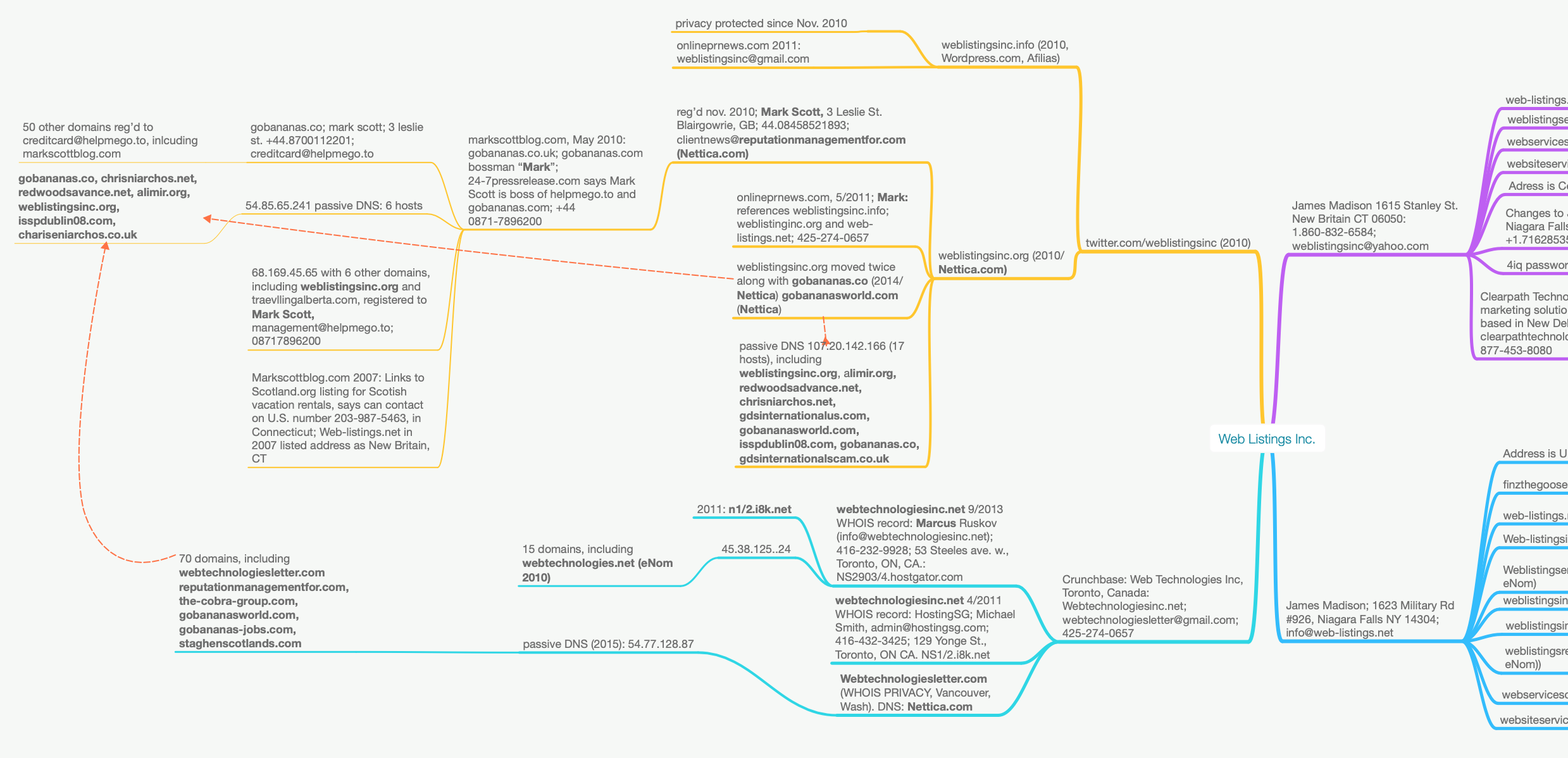
A partial screenshot of a mind map I used to keep track of the myriad connections between various Web Listings domains and their owners. This map was created with MindNode Pro for Mac.
Mark Scott did not respond to multiple requests for comment sent to various email addresses and phone numbers tied to his name. However, KrebsOnSecurity did receive a response from Cobra Group founder Chris Niarchos, a Toronto native who said this was the first he’d heard of the Web Listings scam.
“Mark used to provide some services to us but my understanding was that stopped a long time ago,” Niarchos said. “He used to own a marketing company that we supplied but that contract ended maybe 12 years ago. That’s how we met. After that he did start some internet based businesses where he sold services to us as a customer at arms length. That also stopped many years ago again as we did it all in house. As far as I know he did this for many companies and we were simply a customer of his. In my dealings with him we got what we paid for but never did we have any closer relationship than that.”
USA CONNECTIONS
Two more small — possibly insignificant — but interesting things. First, if we go back and look at archived posts from markscottblog.com in 2010, we can see a number of entries where he defends the honor of Cobra Group, Appco, and other multi-level marketing programs he supports, saying they’re not scams. If we go back further to 2008 and look at Mark Scott’s profile on Blogger.com, we can see at the bottom of the page a link called “Enquiries and Emails.”
Visiting that link brings up what looks like a public shaming page of emails apparently sent to Mr. Scott from scammers trying to set him up for some kind of fake check scheme in connection with renting one of the U.K. properties listed by his various travel accommodations Web sites. Click the “Contact” tab at the top right of that page and you’ll see Travel Scotland has a U.S. phone number that potential customers here in the states can use to make reservations toll-free.
That number happens to be in Connecticut. Recall that the address listed in the ownership records for many of the Web Listings domains tied to the “James Madison/Mark Carter” identities were for an address in Connecticut.
Finally, I wanted to mention something that has stumped me (until very recently) since I began this investigation a couple of years ago. There are two unexpected domains returned when one performs a reverse search on a couple of different persistent data points in the WHOIS registration records for the Web Listings domains. See if you can spot the odd duck in this list produced by running a reverse search at Domaintools on info@web-listings.net (the contact email address shown on the mailed letter above):
Domain Name Create Date Registrar
finzthegoose.com 2010-08-03 enom, inc.
web-listings.net 2007-04-24 ENOM, INC.,ENOM, LLC
web-listingsinc.com 2015-11-06 ENOM, INC.,ENOM, LLC
weblistingservices.com 2007-04-23 ENOM, INC.,ENOM, LLC
weblistingsinc.com 2014-06-21 GODADDY.COM, LLC
weblistingsinc.net 2016-02-09 ENOM, INC.,ENOM, LLC
weblistingsreports.net 2015-11-06 ENOM, INC.,ENOM, LLC
webservicescorp.net 2007-06-03 ENOM, INC.,ENOM, LLC
websiteservicescorp.com 2007-06-03 —
Ten points if you said “finzthegoose.com.” Now let’s run a search on the phone number for Mark Carter — the phony persona behind all the Web Listings domains registered to the Niagara Falls address — +1.716-285-3575. What stands out about this list?
Domain Name Create Date Registrar
aquariumofniagara.org 2001-01-11 GODADDY.COM, LLC
web-listings.net 2007-04-24 ENOM, INC.,ENOM, LLC
web-listingsinc.com 2015-11-06 ENOM, INC.,ENOM, LLC
weblistingservices.com 2007-04-23 ENOM, INC.,ENOM, LLC
weblistingsinc.com 2014-06-21 GODADDY.COM, LLC
weblistingsinc.net 2016-02-09 ENOM, INC.,ENOM, LLC
weblistingsreports.net 2015-11-06 ENOM, INC.,ENOM, LLC
webservicescorp.net 2007-06-03 ENOM, INC.,ENOM, LLC
websiteservicescorp.com 2007-06-03 —
If you’re picking up an aquatic and marine life theme here, you’re two for two. That is actually the real phone number for the Aquarium of Niagara; the Web-Listings people just for some reason decided to list it in their WHOIS records as theirs.
It appears that a Scotsman named Robert Paul Graham Scott — perhaps Mark’s older brother — was in the same line of work (SEO and advertising) and pimping the exact same companies as Mark. According to a listing at Companies House, the official ledger of corporations in the United Kingdom, Paul Scott was for four years until Sept. 2019 a director in HMGT Services Ltd. (HMGT stands for the aforementioned HelpMeGo.To business).
Paul Scott’s own Internet presence says he lives in Perth — a short distance from Mark’s hometown in Blairgowrie, Scotland. Like Mark, Paul Scott did not respond to requests for comment. But Paul Scott’s Twitter profile — @scubadog_uk — shows him tweeting out messages supporting many of the same companies and causes as Mark over the past decade.
More to the point, Paul’s Website — scubadog.co.uk — says he has an abiding interest in underwater photography, scuba diving, and all things marine-related.
source https://krebsonsecurity.com/2020/03/whos-behind-the-web-listings-mail-scam/
 Nineteen of the weaknesses fixed on this Patch Tuesday were assigned Microsoft’s most-dire “critical” rating, meaning malware or miscreants could exploit them to gain complete, remote control over vulnerable computers without any help from users.
Nineteen of the weaknesses fixed on this Patch Tuesday were assigned Microsoft’s most-dire “critical” rating, meaning malware or miscreants could exploit them to gain complete, remote control over vulnerable computers without any help from users.










 London-based Finastra has offices in 42 countries and reported more than $2 billion in revenues last year. The company employs more than 10,000 people and has over 9,000 customers across 130 countries — including nearly all of the top 50 banks globally.
London-based Finastra has offices in 42 countries and reported more than $2 billion in revenues last year. The company employs more than 10,000 people and has over 9,000 customers across 130 countries — including nearly all of the top 50 banks globally.